Why Enterprises Must Adhere To AWS Best Security Practices & Secure Business-Critical Cloud Applications
Abiding by AWS best security practices minimizes the risk profile of your digital business in the Amazon’s cloud environment. Cyberattacks have cost businesses millions of dollars in the past, in-fact, in some extremely disheartening cases, companies were completely forced out of business. Yes, that’s the extent to which crackers (hackers are good people) can wreak havoc on targets. Every digital business across industry domains, irrespective of their geography, size or infrastructure is vulnerable to cyber threats.
If you spend more on coffee than on IT security, you will be hacked. What’s more, you deserve to be hacked
Richard Clarke
We remember how CodeSpaces (a code hosting service provider using AWS infrastrucutre) had to permanently shut its operations falling prey to a successful DDoS attack. Later in 2017, we saw how a Spanish telecommunications giant, Telefonica, too had to instantly shut its servers & VPNs for hours to mitigate & control the damages unleashed by a ransomware security breach. In another instance, a multi-chain US healthcare company, Medstar Health, was completely wiped-off of patient’s digital data stored in the cloud, including communication pagers. Healthcare cyberattacks can even result in loss of lives. So, the stakes are quite high, enterprise cloud security can not be taken casually anymore.
Why Prioritize Security?
Protecting your customer’s data & privacy as well as securing your application & enterprise needs to be prioritized. Security needs to be embedded into every stage of your digital business, right from designing the application, developing and deploying it on AWS cloud to serving the end-client.
Zoom’s customer base skyrocketed from 10Mn to 200Mn active users in a matter of days, but the digital call & conference company was also slammed for its not upto the mark security & privacy arrangements and faced backlash from its users. Reportedly, 10% of Zoom’s clients stopped using the services after security loopholes were exposed. Three months down the line they claim to have addressed most of the security issues.
But, should an enterprise wait for the crisis to happen? Why not go all guns ablazed and implement best cloud security practices at the design and development stage itself and then iteratively make your AWS cloud environment more robust & secure with time?
IaaS & Executive Concerns
A rising number of enterprises are shifting to IaaS platforms like Amazon Web services (AWS), Google Cloud and Microsoft’s Azure. Also, the majority of new-age enterprises are completely building their business on-cloud. In no-time the number of enterprises on cloud would exceed in count than those on-premises.Traditionally, data & other resources used to reside on-premise but now one of the biggest concerns & challenge for you and other business executives shifting/starting their business on cloud is trusting these cloud provider’s servers with our sensitive data, keeping business applications protected, maintaining the confidentiality & integrity of user data.
Potential threats our business critical applications on AWS
In the following sections we are going to explore the best security practices to build & deploy a high-performing scalable, resilient & secure application on Amazon Web services (AWS).
On a high-level, the first step towards building a resilient & efficient cloud infrastructure and to reduce the risk profile of our environment is to understand the potential threats our business critical applications on AWS needs to mitigate.

AWS Platform Vulnerability
- Though AWS has invested heavily on securing its infrastructure, we cannot totally rule out the possibility of a loophole or some vulnerability, no matter how strong the cyber defence! But this should be the least of any business executive’s concern who is considering to deploy their application using AWS cloud infrastructure. AWS platform is highly secure and it is going to be very hard for any cracker to gain control and compromise with AWS platform itself. Security on AWS is a shared responsibility between AWS & the customer. We shall talk more on it soon.
Denial of Service (DoS) or Distributed Denial of Service Attacks (DDoS)
<RISK>
- DoS or DDoS attacks, in simple language, overwhelms servers & websites with more traffic than the network can actually handle, it could be through fake packets, excessive connection requests, unusual number of incoming messages etc.
- Such attacks, if successful, causes target servers, network, websites or services to go inoperable. And it leaves heavy dent on business revenue & profits.
- Risk profiles for such attacks vary depending on the nature of business. Usually, such attacks are carried out by competitors to hurt your business, activists to expose something or by individual crackers or institutions to ransom money.
<SOLUTION>
- AWS recommends customers heavily concerned with DDoS attacks to enroll into AWS Premium Support services to protect your applications and mitigate the risk of such attacks. You could also add a layer of protection to blacklist IPs at an application level or use services like cloudflare to mitigate the risk. There are some security practices guidelines from AWS to handle such threats, download the security checklist included in the article .
Cryptojacking
- Cryptojacking is a new kind of cyberthreat, it involves breaking into your servers or cloud computing systems and then using your computing power to mine for cryptocurrency. It results in heavy financial losses in the form of extra costs for utilising network and server resources, as well as causes slow services being rendered to clients which may result in loss of business.
- LA Times & Tesla were in news back in 2018 when their AWS S3 bucket fell prey to cryptojackers due to poor configurations of respective buckets and ended up paying thousands of dollars without really using the service. But these are avoidable mistakes (if cloud security practices are strictly followed) and so we recommend expert security advice for any business executive going the cloud way.
Insider Threats
Technology trust is a good thing, but control is a better one.
Stephane Nappo
- Threats are not just from external malicious agents but internal too. Organisational staff with privileged access to your computing environment could be a threat, especially post leaving the company. Negligence from staff members, falling prey to phishing activities etc., can help crackers gain access to your cloud computing environment and exploit it for their own benefits.
- Again, expertise in knowledge of the cloud platform and using available security features of IaaS platforms, right configuration and access management of users can help avoid such threats.
Compliance, Poor Configuration of AWS Resources & Data Breaches
- Verizon Data Breach Investigations Report says, 63% of data breaches are due to compromised account access to IaaS root accounts (weak passwords or leak of passwords), unnecessary privileges to employees i.e., poor IAM configurations and poor cloud environment configurations.
- Organisations often have to comply with regional data regulations & other compliances, GDPR could be a good example. Again, negligence to comply with such rules & policies could cost heavily in the form of fine and loss of trust among customers.
- All these are avoidable if right knowledge and right experience is in control of architecting, developing and deploying applications on cloud.
AWS best security practices
Now, let’s quickly skim through the AWS best security practices & approach to build & deploy your business-critical applications on cloud –
Amazon Web Services (AWS) provides a range of built-in configurable security products and features which customers could leverage to meet security objectives of their cloud applications i.e., secure workloads they deploy in AWS.
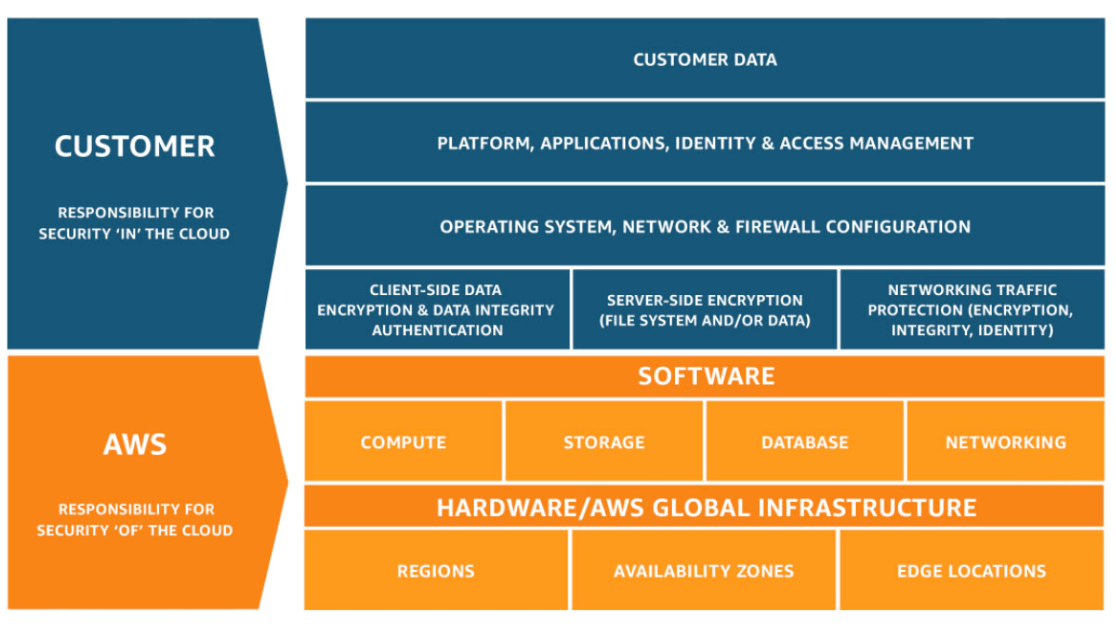
Understand Security as a Shared Responsibility
Security on AWS is a shared responsibility between AWS (security ’OF’ the cloud) and the customer (security ‘IN’ the cloud). As obvious from the below infographic, AWS ensures that the infrastructure services including compute, storage, database and networking services it provides is highly secure & available. Amazon web services also takes up the responsibility for security of its managed services like DynamoDB, RedShift etc.,. Though, it is good to stay updated about security related developments for which AWS is responsible but this should be of least concern to the customer.
The customer shoulders the responsibility of securing its deployed workloads by
- protecting customer data,
- managing, controlling & monitoring access to AWS resources (IAM)
- Configuring network and firewall policies in the right and secure way
- Protecting the network traffic
- Separating & encrypting client-side and server-side data
Security by Design (SbD)
Security by Design is an approach of embedding security & compliance into all phases of security design within the AWS environment through use of standardized, automated, prescriptive and repeatable design templates in AWS CloudFormation.
SbD involves four phases approach which on a high-level could be summarized into :
- Understand your security requirements. Figure out the policies, security rules, control & data compliance that needs to be embedded into your application to make it function in a protected and secure way.
- Build a rightly secured environment in-line with phase 1. Define required configurations, data encryption requirements, control, access and monitoring of AWS resources.
- Enforce use of secure environment template through AWS service catalog.
- Perform validation and auditing activities.
Authentication & Resource Access Management practices :
1. Protect & secure your root account :
- Use a strong password for AWS Management Console
- Consider using a password management tool like AWS secrets Manager for storing database passwords
- Enable multi-factor authentication
- Setup strict account password policy for IAM users to boost security against brute force attacks
2. Secure & control access to AWS resources :
- Setup IAM policies and attach it to ‘groups’ & ‘roles’ for managing & controlling access permissions of AWS resources
- Avoid programmatic access to your AWS resources using access keys associated with your root account
- Create IAM users with specific permissions for required APIs
- Make sure IAM users have only necessary privileges required to deliver their responsibility and no extra privileges
- Enable IAM users for multi-mode access to mitigate password or access key compromise threats
- Rotate IAM access keys on a regular basis to mitigate the risks of compromised/lost access key
- Remove not-in-use IAM access keys and disable inactive/not-required IAM users
3. Avoid using expired SSL/TLS certificates
4. Use AWS control tower to setup and govern a multi-account AWS environment. Multi-account environments help in separating data & resources at production and non-production stages.
Secure Configuration of AWS resources best practices
- Ensure EC2 security groups don’t have large ranges of ports open
- Restrict large IP ranges from inbound access to EC2, allow only specific individual IPs
- Reduce the number of discrete security groups, IAM groups
- Use secure SSL ciphers & versions for establishing connection between the client and the ELB load balancer.
- Delete not-in-use SSH keys and rotate SSH keys periodically
- Restrict access to AMIs, RDS instances, Redshift clusters etc.,. Ensure well known ports for SSH, FTP, DNS and others are available to required entities only.
Monitoring, Detection & Responding to incidents best practices
- For tracking AWS environment enable AWS CloudTrails in all availability zones, regions. Cloudtrail keep tracks of almost all the activities in the cloud. You can log API calls for your account through AWS management console, SDKs, CLI tools and multiple other resources. It can even pin-point to specific IPs making the request.
- Use Cloudwatch & GuardDuty as a threat detection & Alert service. Cloudwatch help you track & identify unauthorised behaviour. Also, we can configure for automated response and can notify individuals about activities. This can help troubleshoot security issues, if need arises.
- Configure cloudtrail to enable logging at both application and service level i.e., enable S3, VPC, ELB, Redshift level logging.
- Ensure you have incident response (IR) plan & regularly practice responding to incidents by simulating attacks and utilize the learning in continuously improving your security.
Infrastructure & Data Protection best practices
- Use AWS systems manager patch manager. Automate the process of patching managed instances including OS, Applications and your code with both security related and other types of updates.
- Use Amazon Cloudfront, AWS WAF and AWS Shield to provide protection from DDoS attacks
- Configure Security groups to control inbound and outbound traffic
- Group resources into subnets to create routing layers
- Protect data at rest by encrypting EBS volumes & S3 buckets, use AWS Key Management Service to protect data across AWS services and your application.
- Encrypt data in transit for all network traffic
- Avoid giving users unnecessary access to databases, use Amazon Quicksight dashboard to give access to data for business users
Compliance
- AWS is an accredited environment
- All AWS services can be used in compliance with GDPR contractual obligations and other industry level compliances as required.
Traditionally, enterprise data and resources mostly resided on-premises. Adoption of these IaaS platforms is increasing with time. Much of the growth is attributed to the flexibility, scalability and cost optimization benefits cloud offers businesses. And with growth of IaaS, the scope of cyber threats are broadening too. So, it’s critical to develop your business application on the cloud in the most secure way. Prefereably, embed security at every stage of product development and service delivery. Codewave cloud ninjas, with more than 7 years of expertise, could help you navigate your cloud journey in the safest and smoothest way. Contact our experts to brainstorm further.
Frequently Asked Questions(FAQs)
1. What are the top security best practices for protecting my AWS infrastructure?
The top security best practices for protecting your AWS infrastructure include:
Using IAM to control access to your resources, using security groups and network ACLs to control inbound and outbound traffic, Using encryption to protect sensitive data, using CloudTrail to monitor and audit activity in your AWS environment, and regularly reviewing and updating your security configurations. Additionally, it’s recommended to use AWS security services like Amazon GuardDuty, Amazon Inspector, and Amazon Security Hub to protect your infrastructure.
2. How can I secure my data in AWS, and what are the best tools to use?
Securing data in AWS can be done by using encryption for data at rest and in transit, using IAM policies to control access to data, and using security services such as Amazon S3 bucket policies and AWS Key Management Service.
3. What are the best practices for securing access to my AWS resources, such as IAM policies and security groups?
Best practices for securing access to AWS resources include: using IAM roles and policies to grant least privilege access, using multi-factor authentication for privileged users, using security groups and network ACLs to control inbound and outbound traffic, and regularly reviewing and updating IAM policies and security group rules. It’s also recommended to use IAM roles for EC2 instances and use AWS Secrets Manager to rotate, manage and retrieve secrets. Additionally, using AWS Organizations to centrally manage and govern your accounts and resources, and using AWS Resource Access Manager (RAM) to share resources across accounts can also help to secure access to your resources.
4. How can I ensure compliance with industry standards and regulations when using AWS for my business?
It is recommended to use AWS services such as AWS Config and AWS Compliance Manager to monitor and assess the compliance of your AWS resources. Additionally, you can use AWS Artifact to access compliance reports and attestations from AWS. Using AWS services such as Amazon S3 Object Lock, AWS Key Management Service, and AWS Certificate Manager to protect sensitive data also helps to comply with regulations. AWS also provides several compliance-specific solutions like AWS GovCloud (US) and AWS Secret Region to meet specific regulatory requirements.